“Attackers think in graphs; defenders think in lists.” These words from John Lambert at Microsoft capture a core cybersecurity challenge: attackers exploit interconnected vulnerabilities, while defenders analyze isolated data points. What if defenders adopted the attackers’ approach by visualizing and understanding these connections in real time?
Our mission with Threat KG (Knowledge Graph) is to leverage knowledge graphs for proactive threat defense. It integrates CMDB data and other sources into a labeled property graph of enterprise assets, vulnerabilities, threats, and incidents—creating a single source of truth for security teams. Continuously updated through log parsing and data feeds, it leverages large language models (LLMs) to extract and refine cybersecurity insights. This graph-based approach enables prioritized context-driven responses improving security efficiency and resilience.
Here’s how it works.
From Lists to Relationships: The Power of Knowledge Graphs in Cybersecurity
Traditional CMDBs store data in structured rows and columns, which can lead to a fragmented view of assets, vulnerabilities, and incidents. This limited approach often leaves defenders combing through siloed data, making it difficult to understand how vulnerabilities might cascade through an interconnected network of assets.
By shifting from a traditional database to a knowledge graph, Threat KG provides a holistic view of cybersecurity risks. Instead of isolated analysis, defenders uncover relationships between assets, assess vulnerability impact on business-critical services, and map potential attack paths. In other words, we’ve given defenders the attacker’s perspective, allowing them to see not just where an attack might occur but how it might spread—and what needs protection most urgently.
Imagine this scenario: a new exploit is identified for a specific asset type. With a traditional approach, defenders would likely review lists and try to trace the risk manually. However, with Threat KG, a simple query instantly reveals all related assets, associated vulnerabilities, and potential impact areas. This enables defenders to map out possible attack paths and prioritize mitigations where they will have the greatest effect.
Bringing All Relevant Data into One View: From Logs to VAPT Assessments
As shown in Figure 1, Threat KG goes beyond CMDB data, integrating multiple sources to deliver a real-time security landscape.
Cybersecurity relies on two key types of logs:
- Continuous Logs: Generated in real time by network devices, internet activity, and security tools, offering continuous visibility
- Time-Interval Logs: Captured during Vulnerability Assessment & Penetration Testing (VAPT) or security audits, providing snapshots of vulnerabilities.
Traditionally, VAPT logs from tools like Nmap, Nessus, and Nikto were archived post-assessment, resurfacing only during future audits. But by adding VAPT data into Threat KG, we’re transforming these assessments into a living part of our security landscape. Vulnerabilities from VAPT scans are no longer forgotten; they remain actively available in the graph, connected to associated assets and constantly updated with new information.
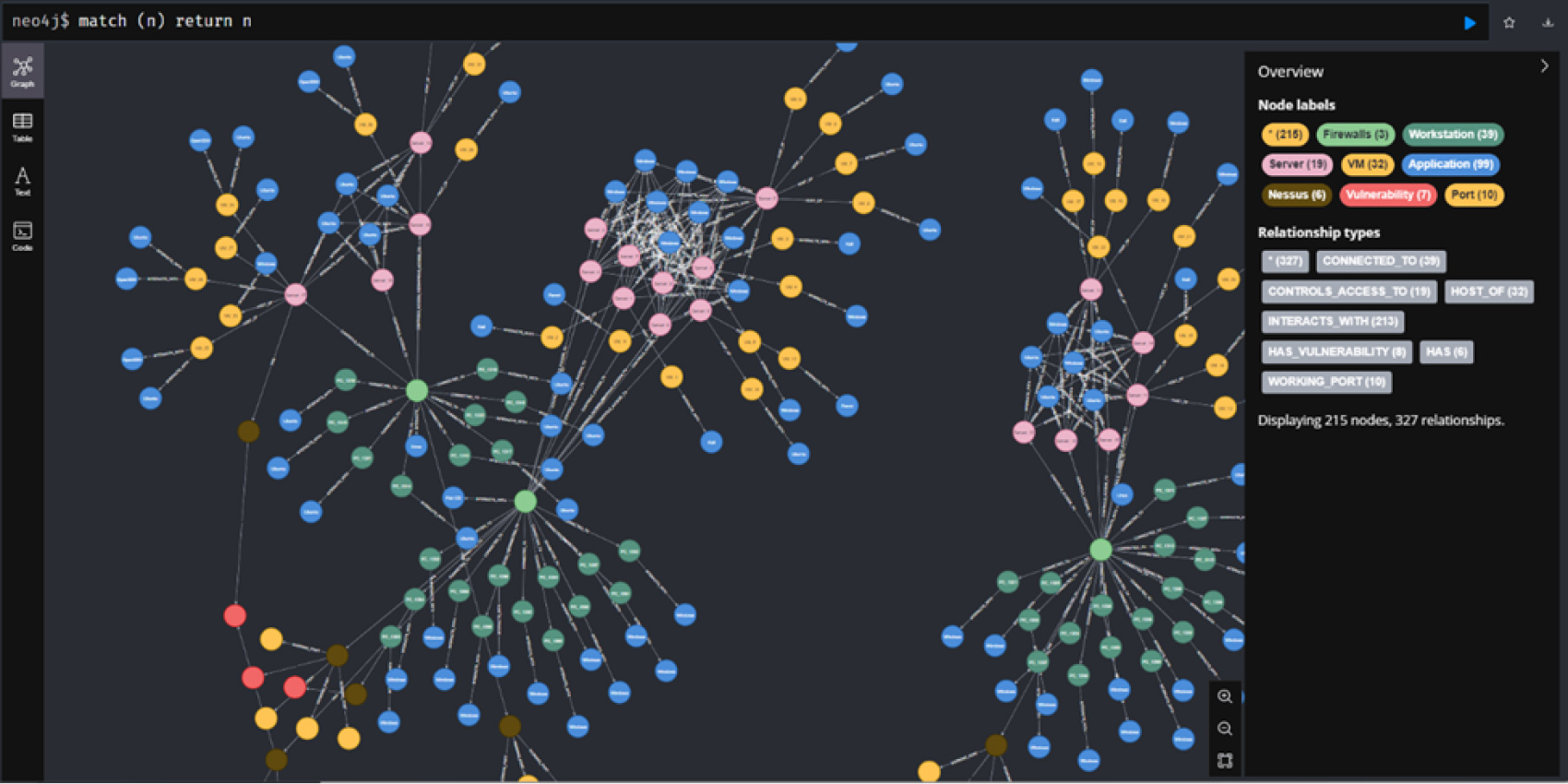
Figure 1 – Depicts Schema – This picture shows a visual representation of how different computer systems, applications, and vulnerabilities are connected and interact with each other in a network. So instead of storing CMDB in lists, KG provides better visualization
Prioritizing with Intelligence: How Graph Algorithms Empower Threat KG
Threat KG leverages advanced graph algorithms to help defenders prioritize actions and optimize threat response.
- Centrality Algorithms: Identify the importance of each node in the knowledge graph. Critical servers or assets with high centrality scores are prioritized as they are deeply interconnected and influential, helping defenders focus on key pathways attackers might exploit.
- PageRank: Assigns an Asset Priority Score to each asset in Threat KG, reflecting its importance based on connectivity and role. Assets with high PageRank scores are prioritized for security due to their potential impact on the network.
- Path Finding: Utilizes the Dijkstra Shortest Path algorithm to determine the shortest path between assets. This algorithm employs the Asset Priority Score as weights. It calculates the shortest path between a source and target node specified by the user.
This algorithm-driven approach prioritizes vulnerabilities based on their impact on our most critical assets, ensuring defenders focus resources where they matter most.
The Real Benefits of Threat KG: Proactive Defense and Efficient Response
As shown in Figure 2, by integrating knowledge graphs, Threat KG brings a host of benefits to our cybersecurity efforts:
- Persistent Vulnerability Awareness: Vulnerabilities identified in VAPT exercises are no longer forgotten but are continually available and updated within the graph, connected to their associated assets. This helps us maintain a long-term, context-rich view of risk across our network.
- Pattern Recognition and Trend Analysis: With all vulnerability data connected in Threat KG, defenders can quickly identify recurring vulnerabilities, spot weak points in defenses, and recognize patterns over time. This visibility allows us to adjust defenses dynamically and stay a step ahead of evolving threats.
- Faster, Context-Driven Response: Threat KG enables defenders to trace attack paths, assess impact, and respond appropriately. Because the knowledge graph shows each vulnerability and threat as part of an interconnected web, defenders gain a comprehensive view of the situation and can respond proactively and precisely.
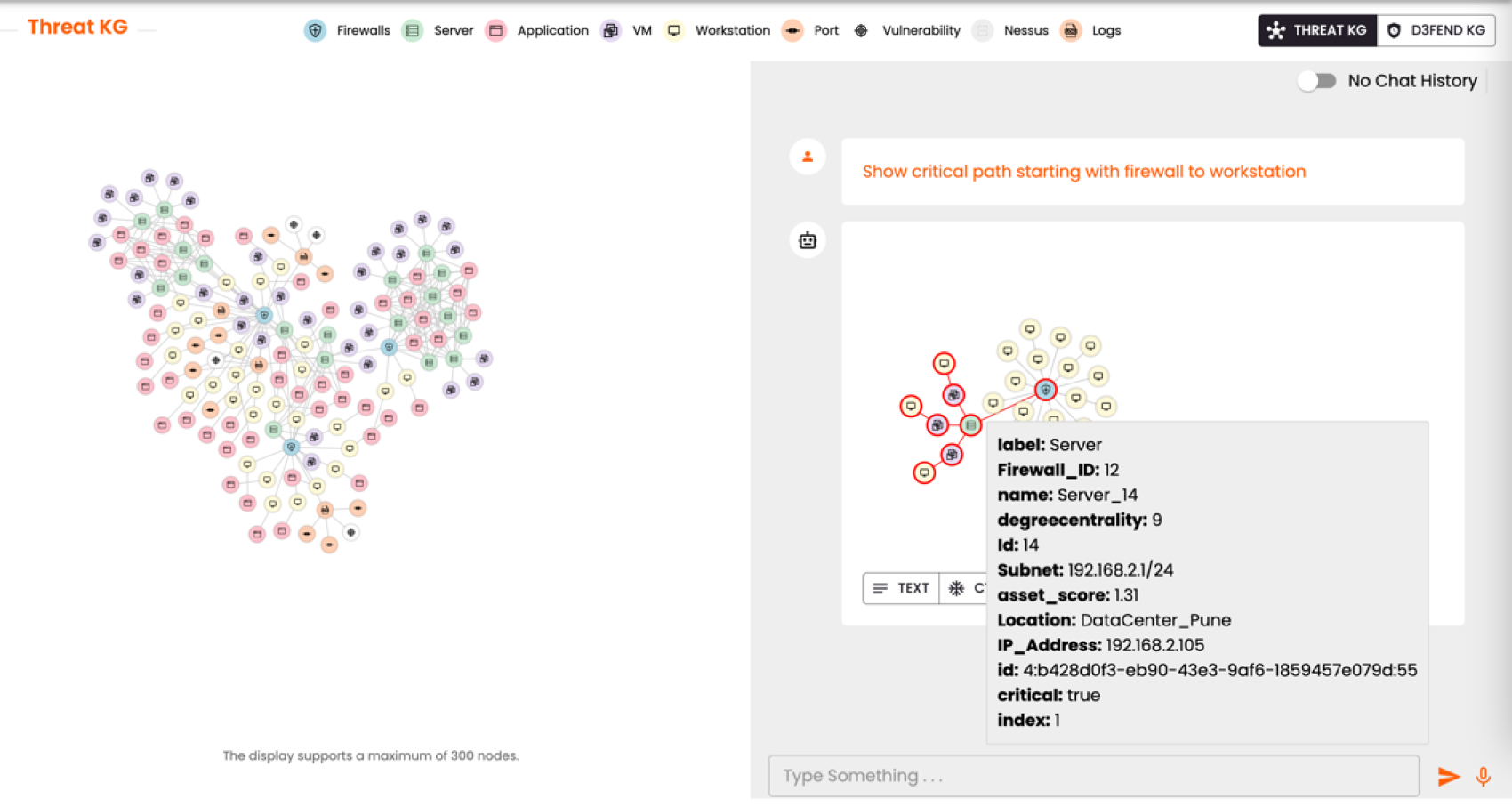
Figure 2 – Depicts Threat KG – How Persistent’s Threat KG looks with Graph visualization and NLP querying capabilities
Ultimately, Threat KG changes the game for cybersecurity solutions by empowering defenders to think in graphs instead of lists. With insights derived from centrality, PageRank, and Vulnerability Priority Scores, we’re not only visualizing relationships but understanding the hidden connections and risks in our network.
Attackers exploit complex paths and vulnerabilities within interconnected environments, and Threat KG helps us stay one step ahead by allowing us to see the same connections they do. With Threat KG, our defenses are no longer limited to reactive measures; we can prioritize, detect, and mitigate threats more strategically and effectively. In a world where cyber threats continue to grow in sophistication, Threat KG brings defenders the tools they need to secure systems with intelligence, precision, and foresight.
Threat KG redefines cybersecurity, enabling smarter defense, better prioritization, and proactive threat mitigation. Contact us to learn more.
Author’s Profile
Venkateshwar Tyagi
Senior Consulting Expert, Corporate CTO Organization BU







