In the rapidly evolving digital landscape, securing APIs has become paramount for organizations to safeguard sensitive data and protect against cyber threats. One of the innovative approaches to enhance API security is introducing a dynamic and time-bound mechanism to generate and validate one-time tokens for API access, providing an additional layer of protection against unauthorized access and potential data breaches. In this article, we explore the significance of the accelerator in securing APIs and its potential to fortify the overall security posture of modern enterprises.
When an API is secured using a bearer token generally valid for a few minutes based on the configuration, the API Gateway, which enforces token validation policy, validates the token and provides access to the API.
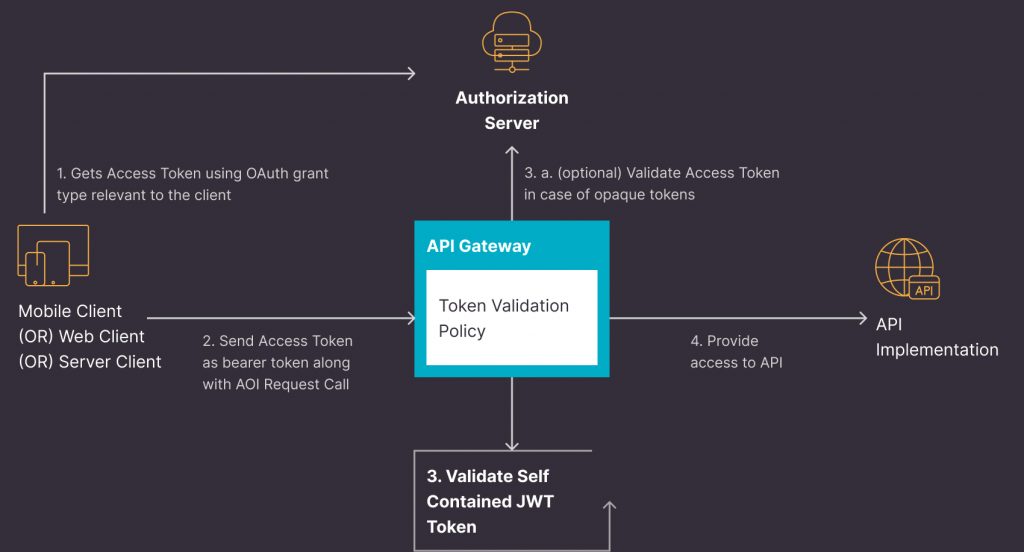
This token can be of two types:
- Opaque Token
- Self-Encoded token like JWT
To validate the Opaque token, the API Gateway must communicate with the Authorization server issuing the token. In case of In case of JSON Web Token (JWT), the API Gateway can verify the signature and validity of the token without contacting the Authorization server.
It is possible that malicious users can sniff this token and can use the token with man in the middle (MITM) or replay attack to get access to API. To avoid these attacks using tokens issued by the Authorization server, we can take the following actions while considering some caveats:
- Opaque Token: If the authorization server provides an end point for token revocation, the API gateway can invalidate the token as soon as token introspection is done by calling the token revoke endpoint. This requires an additional call to the authorization server. In addition, there is no out-of-the-box policy available that can revoke token after token is validated.
- JWT: Even if the JWT is invalidated by calling the revoke end point, the client/malicious user can continue to use that token until token expiry time, as JWT is Self-Encoded and we don’t contact the Authorization Server to validate JWT.
To address this problem of MITM (or) replay attacks, i.e., to restrict token usage (especially JWT as it is self-encoded) to only one time, Persistent has created a custom policy to allow only one-time usage of JWT. This accelerator can be altered for opaque tokens as well.
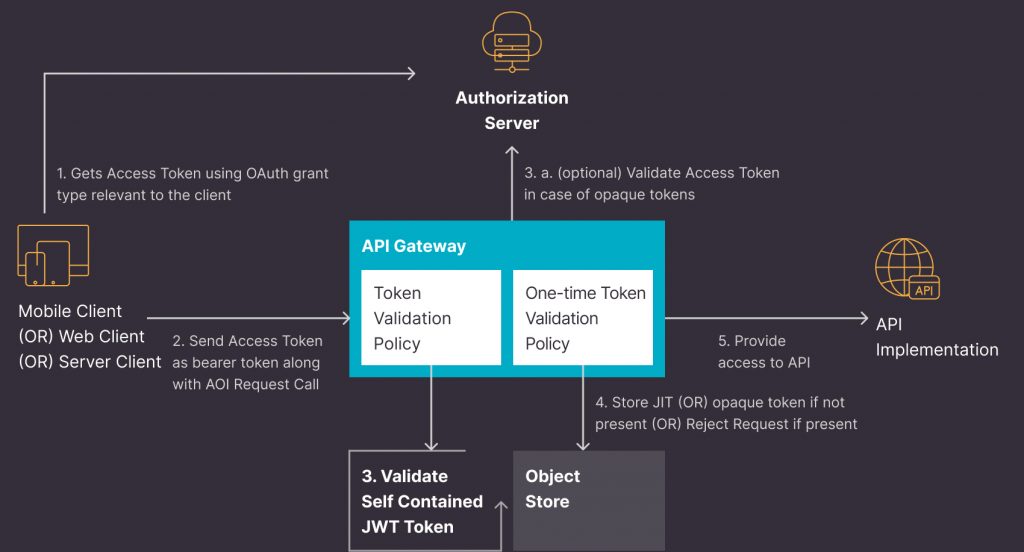
Below are the features of our One Time JWT Policy:
- Restrict the usage of a JWT only once to avoid attacks, which is very important for critical transactions like financial transactions (e.g., money transfer, bill payment, order processing, etc.).
- This policy is stateful, as this needs to maintain the list of JWT to know whether token was already used.
- The state (list of JWT) must be distributed when we have multiple instances of the API deployed for high availability/throughput. We need to clear the state at regular intervals to free up the memory.
This custom policy is implemented using:
- Object Store to store JIT ID extracted from JWT; with every request JIT ID is extracted and seen if it is present in OS; if JIT is present, then it is an attack by a malicious user and the API access is denied.
- Object Store is set to Persistent store so that it is available across different workers on CloudHub (or) different nodes in a cluster.
- TTL for JIT ID Object Store can be set to the expiry time of the JWT so that JIT ID Object Store is cleaned up at regular intervals.
Organizations that prioritize API security and embrace security measures through such accelerators will be better equipped to thrive in an increasingly interconnected and data-driven world. They can assure their customers and partners that their data and transactions are safeguarded by cutting-edge security measures. Implementing this accelerator paves the way for a more secure and resilient API ecosystem, ultimately fostering long-term business success.
Persistent is committed to providing its clients with accelerated and efficient solution development through our cutting-edge accelerators. By leveraging these accelerators, clients can expedite go-to-market and rapidly address their business challenges. By partnering with Persistent and harnessing the power of its engineering prowess, clients gain competitive advantage, achieve faster ROI and stay ahead in their respective markets by rapidly developing innovative and value-driven solutions.






