Decades ago, separate teams within networking managed LAN infrastructure, wireless network, WAN connectivity, and voice infrastructure. A different cybersecurity team handled firewalls, antivirus, proxy, security log management, and observability with intrusion detection systems. There was a clear-cut distinction between teams managing different aspects of enterprise networks and security.
The first consolidation happened in the networking domain with the advent of graphical user interfaces that enabled a single networking team to manage LAN, wireless, and WAN infrastructure. Subsequently, network engineers started designing firewall architecture, embedding them within the network infrastructure in enterprise datacenters.
Recent years have seen a significant shift in network and security management, largely driven by the rise of Zero Trust Network Access (ZTNA). These architectures, designed to combat coordinated cyberattacks, have paved the way for a new era of security-embedded, network-heavy technologies such as Secure Access Service Edge (SASE), Security Service Edge (SSE), and micro-segmentation. SD-WAN, a network connectivity solution, takes this consolidation a step further by integrating security features into the network stack.
With ongoing security threats, the lines between network and security have blurred, giving way to a consolidated framework that becomes the de facto operating protocol for modern enterprises, one that demands attention from company leaders.
Factors that Contributed to Network-Security Consolidation
The ubiquity of public cloud infrastructures widened the network perimeter and made security a top priority as enterprise data and applications moved from controlled on-premises datacenters to shared IT environments. Cloud-native solutions require DevOps pipelines to build landing zones and the entire cloud network infrastructure with various connectivity options back to the datacenter. The focus shifted to Identity Access and Management (IAM), Application Security, Endpoint Detection and Response, e-mail, and Security Operations Center to provide security controls.
Moreover, the steady proliferation of security threats at every layer of the enterprise IT infrastructure called for additional security layers and measures throughout enterprise networks. Traditional network architectures comprised a solid two-tiered perimeter consisting of multi-vendor firewalls, an antivirus system, a proxy for internet traffic, and a stateless access control list (ACL)-based access on LAN segments. ACLs got messy with complex network architectures with requirements for creating multiple isolated LAN segments, so stateful firewalls came into the mix (Cisco’s Firewall Service Module, built into catalyst switches, is one example). This transition to full-fledged firewalls with isolated LAN segments enabled network engineers to manage firewalls.
The Way Forward
Gartner defines a firewall as an appliance with the following core and optional capabilities, showing the intertwined nature of network and security firewall as an appliance with the following core and optional capabilities, showing the intertwined nature of network and security:
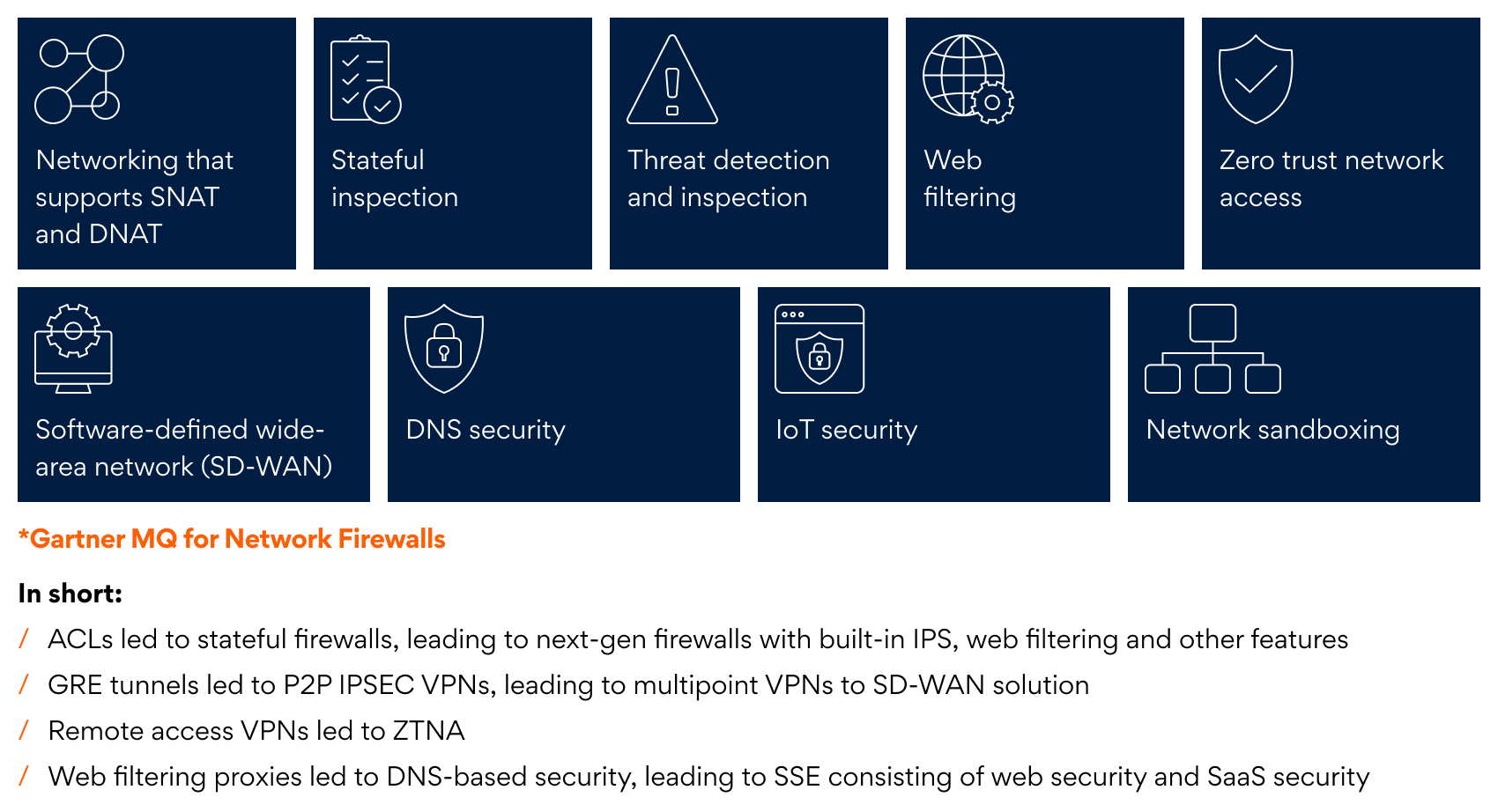
As enterprise working environments evolve with trends like BYOD (bring your own devices), remote work, hybrid cloud architectures, and the explosive growth of SaaS platforms, so does the constant risk of cyber threats and breaches. Since network connectivity is at the core of this transformation, building security into every layer of connectivity is imperative.
Technology consolidation is the norm, so we’re quickly seeing the emergence of single-vendor-SASE — one appliance or fabric of service-chained network function virtualization providing functionalities such as firewall, SD-WAN, web filtering, cloud access security broker (CASB), ZTNA, sandboxing, and browser isolation.
While IT teams scramble to keep up with the pace of this colossal expansion to provide the best performance for end users, securing data is business critical. The enterprise approach to network and security is constantly changing, and instead of jumping on the bandwagon, enterprises need to approach it strategically.
Persistent, a leader in enterprise networking and security solutions, offers a portfolio of managed network security services that trigger:
- Cost Efficiency: Eliminate the cost of hiring, training, and maintaining in-house IT staff with our managed network and security orchestration services, which optimize operational spending on hardware and software upgrades.
- Accelerated Transformation: Enhance digital capabilities and user experiences with high-speed, reliable, and secure connectivity offered by our cloud-first network management solutions, which fast-track the implementation of software-defined networking (SDN) and network function virtualization (NFV).
- Enhanced Performance and Security: Steer clear of cyberattacks, data breaches, and compliance issues with embedded best practices and gold standards within enterprise network infrastructure and IT operations, backed by our expert-led design, deployment, and monitoring solutions.
- AI-Driven, Automated Network Management: Benefit from automated configuration and network analysis for improvement, troubleshooting, and maintenance with minimal human intervention.
To ensure connectivity with robust cybersecurity, get in touch with us here.
Author’s Profile
Hariprasad Sundaramurthy
Practitioner, Security Practice







