The 2023 IBM Cost of Data Breach Report pegs the monetary risks of a single data breach at $4.5 million. These are high stakes with a looming recession, rising inflation, and mounting geopolitical tensions. Banking and insurance firms appear to be on the radar, while healthcare firms report the most expensive data breaches at an average cost of $10 million in damages. Cybersecurity threats are no longer a rookie game; they have evolved into sophisticated attack machinery that can destabilize enterprises, governments, and individuals.
The repercussions go beyond financial losses and trickle down as far-reaching impacts on reputation and customer trust. In April of this year, Capita, a UK-based outsourcing giant, confirmed a cyber-burglary where intruders infiltrated IT systems undetected for nine days. Some 0.1% of Capita servers were accessed, and it had evidence that data, including personal and corporate information, had been exfiltrated. A law firm that sent a Letter of Claim to Capita has signed up nearly 1,000 clients as it prepares a class action lawsuit.
Threat factors increase as enterprises open their data and systems to the cloud, integrating with different entities in different regions. The IBM report also found that eight of every ten breaches involve data stored in the cloud. Add to that the regulatory push to penalize enterprises for breaching sensitive information related to customers or users, with fines running into hundreds of millions of euros under a single European Union law – the General Data Protection Regulation (GDPR).
How to fix this drain?
Digital transformation has rendered enterprise data more integrated, interconnected, and interoperable, breaking down traditional security barriers and resulting in an exponential rise in failure points. Enterprises need a 360-degree approach to address this new threat that arises out of a widely exposed, vulnerable surface. Here is a seven-step security strategy to preempt data breaches:
- Discovering and Classifying Sensitive Data: Data discovery and classification solutions enable enterprises to identify and classify sensitive data within their environments. Employing automated scanning and classification techniques can help provide comprehensive visibility into data landscape, identify potential risks, and implement appropriate security measures. Persistent offers robust data discovery and classification tools to protect valuable data assets.
- Data Encryption: Data encryption is an essential line of defense that renders data unreadable to unauthorized individuals. Whether data is at rest (stored on servers or devices) or in transit (being transmitted between systems), employing encryption technologies ensures that even if data falls into the wrong hands, it remains inaccessible and unintelligible. Persistent provides robust encryption solutions to protect data integrity and confidentiality throughout its lifecycle.
- Data Loss Prevention (DLP): These are designed to detect and prevent unauthorized transmission or leakage of sensitive data. Enterprises can establish granular control over data movement by employing DLP solutions, applying content-aware policies, and preventing data breaches or accidental data loss. Persistent assists in implementing effective DLP strategies and safeguarding critical information from unauthorized disclosure or theft.
- Data Masking: This technique obfuscates sensitive data by replacing it with realistic but fictitious data. This enables enterprises to use realistic data for non-production purposes, such as development and testing, without compromising security. By implementing data masking solutions, businesses can protect sensitive information while maintaining its usability for various operational needs.
- Database Activity Monitoring (DAM): This technology provides real-time monitoring and auditing capabilities, enabling enterprises to track database activities, detect suspicious behavior, and respond swiftly to potential threats. Enterprises can continuously monitor database transactions and user activities to identify unauthorized access attempts, data manipulation, or abnormal patterns, ensuring data security, and compliance.
- Public Key Infrastructure (PKI): This framework facilitates secure communication with digital certificates and encryption. By employing asymmetric encryption algorithms, PKI ensures data authenticity, integrity, and confidentiality. Persistent’s PKI solutions, including certificate management and secure key storage, help establish a trusted infrastructure for secure data exchange and authentication.
- Certificate Management: Effective certificate management is crucial in hybrid IT environments to ensure the security and validity of digital certificates used for encryption, authentication, and secure communication. Persistent specializes in certificate management solutions across diverse environments, ensuring consistent data security.
How Persistent can help bolster data security posturing
Security can burden businesses by usurping resources and bandwidth, diluting focus from innovation and core business activities. It is also a specialized field that requires out-of-the-box thinking and hard-to-find niche skills to strategize and plan security frameworks that keep ahead of the bad actors. Persistent, with its three-decade-long engineering legacy, can help enterprises be prepared to ward off a security threat. Our data security veterans have created a framework embedded with accelerators and industry-aligned tools to ensure 360-degree data protection. Our framework comprises:
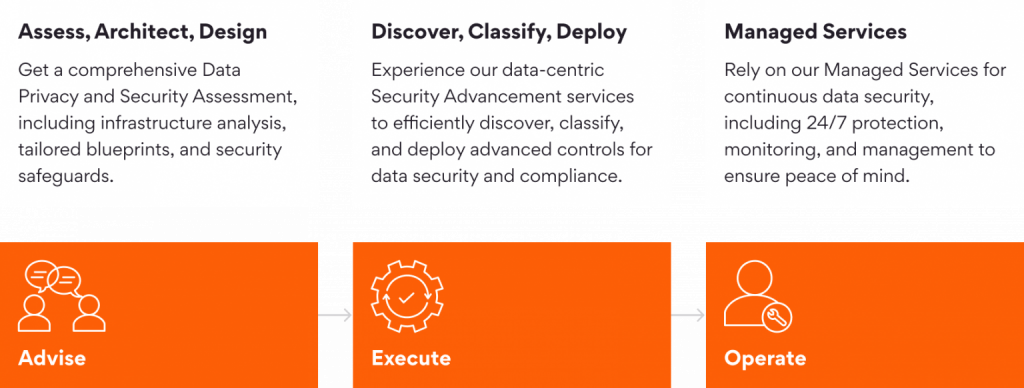
- Security Assessments: In-depth evaluation of existing data security infrastructure to identify vulnerabilities and develop a roadmap for improvement.
- Policy and Procedure Development: Creating robust data security policies, procedures, and best practices aligned with industry standards and regulatory requirements.
- Incident Response and Remediation: Developing incident response plans and providing swift and practical assistance for minimal disruption and optimal recovery.
- Technology Implementation: Recommending and implementing advanced data security technologies, including database firewalls, encryption tools, DLP and more
Secure and protect your enterprise data with Persistent. Contact us here.






