“Stringent compliance laws and a boost in data analytics have made consent-based data management critical. With the growing complexity in managing privacy policies, businesses need to ensure strict policy enforcement.”
– Swapnil Mehta
With ever-increasing consumer awareness and mandates by regulators, businesses are seriously looking into the privacy of information. As data breaches and unauthorized leaks continue to raise awareness and expectations around data security and consumer privacy rights, data protection regulations have raised the bar for the way companies protect personal data.
The push for consent basis storage and usage of information (PII & non-PII) has led to setting up of privacy policies by most businesses. According to Gartner, today, fewer than 50% of documented corporate strategies mention data and analytics as fundamental components for delivering enterprise value. By 2022, 90% of corporate strategies will explicitly mention information as a critical enterprise asset and analytics as an essential competency. Hence, it is a crucial time for businesses to set up data governance structures.
Challenges that are often overlooked
We interacted with the attendees at the IDENTIFY event. Below are our introspections for data privacy and governance approach businesses are following –
Most businesses have already set up governance structures, and data privacy offices but is that ensuring enforcement of their policies? Our experience indicates that a lot of work is being done with regards to privacy office setup, policy definitions, data discovery, registry and classification but the real switches and gates for enforcing governance and policy controls are missing. Also, companies need to ensure that these policies are being adopted and enforced throughout the technology stack of organizations.
Many organizations lack the know-how or the platforms to enable rich policy-based controls that are resulting from certain attributes and are influenced by contextual information. Externalization of such controls is going to hold the key to enabling real privacy gate-keeping while providing the stakeholder’s ability to fine-tune knobs of their policies in an agile and business-friendly manner.
How to tackle these challenges?
Businesses should focus on the topic of how to make privacy policies actionable. As a part of this drive, they should work on models and solutions that take the privacy mandates & policies and provide –
- The tools and means to enforce the controls
- A watchtower to keep an eye on the controls
- An ability to simulate situations to understand the behavior of those controls
- Validation of the efficacy of the controls
While keeping an eye on policy enforcement, it’s critical to ensure the following:
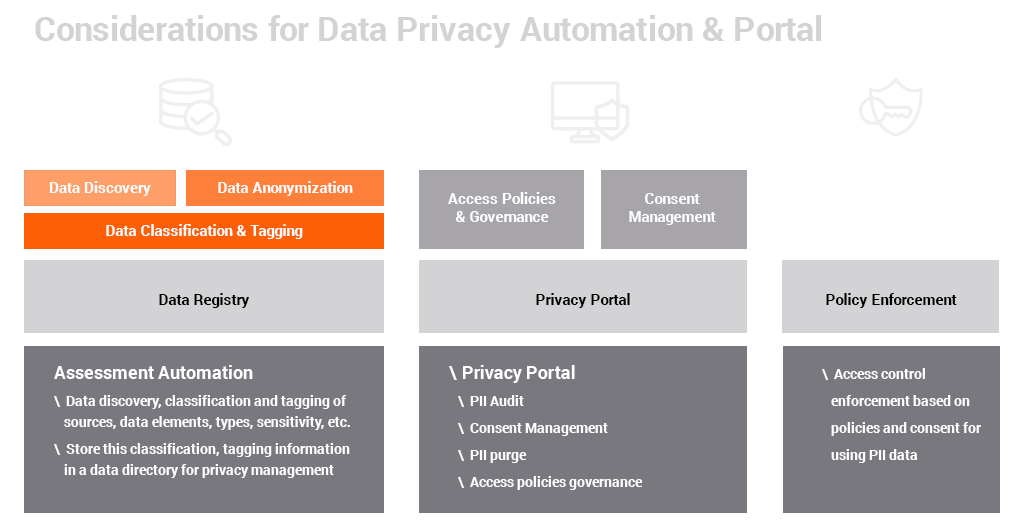
- Automating discovery, classification, and tagging of data held in enterprise repositories
- Creating a registry that contains an inventory of sensitive information
- Helping to review and audit access to personal data and manage consent through the privacy portal
This will not only help businesses manage data privacy & consent better but also take the burden off the developers. However, these are key focus areas for most of the data security decision-makers today.
We put together solution/s that make it easy to externalize the controls while giving the business ability to tweak the privacy switches, without having to go through a code change cycle. Additionally, the solution design should promulgate & facilitate concepts of Privacy by Design (PbD), thus making privacy an integral part of processes and technology/application stack.
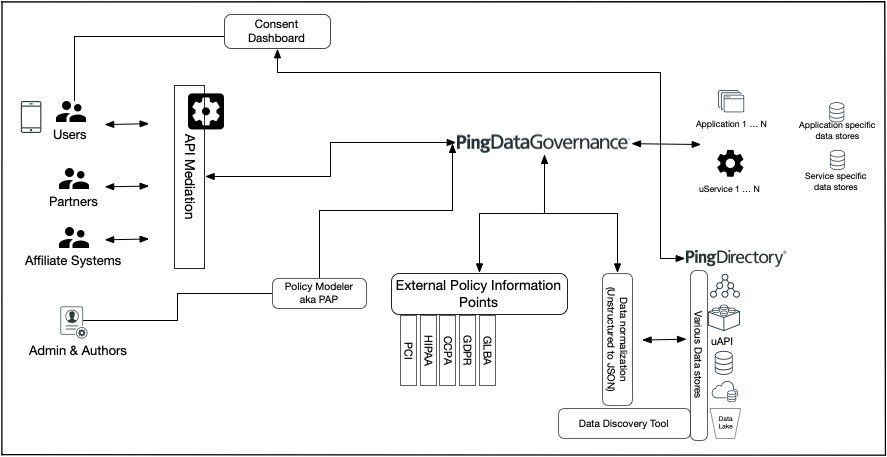
Nearly all privacy-focused regulations have two macro components, consent capture which is akin to modeling peer to peer entitlements and having a system of enforcing them whilst providing accountability.
Ping Identity provides a highly scalable and flexible data store, that is well suited to model and store consent data. It’s flexible schema using JSON attributes allows for a variety of data type representation. It comes with a specific base class for storing consent, which allows for multiple consent values for each user, where each value can be acted upon independently. Additionally, it is possible that other entitlements such as delegation may reside in systems outside of Ping Directory for legacy reasons, which may need to be acted upon, updated or taken into account. Ping DataSync, which comes with Ping Directory can handle real-time bidirectional sync between these systems.
For continuous monitoring and enforcement, Persistent leverages Ping Data Governance allowing for;
- Decoupling of data access policy from each individual application, thus eliminating the risk of accidental exposure of data due to an errant API
- Consistent modeling and enforcement of the policy, avoiding unforeseen policy conflicts
- Up to date modeling of policy rules as regulations change without impacting applications
- A central audit trail to prove compliance
- An easy to use business user-centric policy editor
With these tools, Persistent helps clients better understand best practices around governance and data security measures and setting up data governance with a focus on compliance.
Learn more about our Data Access: Governance & Privacy offering. To schedule an assessment, write to us on info@persistent.com
Find more content about
Data Governance (5) data security (5) Data Privacy (2) Privacy (1) Regulatory Compliance (1)