
Information Security
Information Security at Persistent Systems
Persistent Systems Limited (PSL) operates across multiple business verticals, each catering to distinct customer requirements. With a diverse portfolio spanning industries such as healthcare, financial services, technology, and manufacturing, PSL encounters a wide range of customer needs and expectations. From developing custom software solutions to providing consulting services, PSL’s business activities are tailored to meet the unique demands of each vertical. This diversity in business verticals and customer requirements underscores the complexity of PSL’s operations and highlights the need for agile and adaptable strategies to effectively serve its diverse clientele. Through a combination of innovative technologies and industry expertise, PSL strives to deliver tailored solutions that address the specific challenges and opportunities faced by its customers in various sectors.
PSL’s CISO office remains vigilant in safeguarding the company’s assets and reputation. By prioritizing information security and promoting a collective responsibility for safeguarding sensitive data, PSL demonstrates its commitment to maintaining the trust and confidence of its customers and partners.

“In the current evolving threat landscape, Cyber threats are becoming increasingly sophisticated, organizations require a holistic cybersecurity program to not only prevent cyber-attacks but also detect, respond, and recover in a timely manner. At Persistent, our Cybersecurity program is driven by robust cyber resilience, cutting-edge security measures, a culture of security awareness, and compliance with industry standards and regulations while enabling the company to achieve its business goals and objectives.”
Devender Kumar
Chief Information Security Officer
Enabling CIA Triad Through Information Security Management System (ISMS)
To bolster trust in our commitment to information security, Persistent has implemented an Information Security Management System (ISMS) certified under ISO 27001. This framework guarantees:
- Confidentiality: Only authorized users with legitimate need-to-know access can retrieve sensitive data, reducing the risk of inadvertent leaks or deletions.
- Integrity: Ensuring accuracy and completeness throughout the data lifecycle, preventing unauthorized modifications.
- Availability: Facilitating access to information and critical systems for authorized users through robust business continuity plans.
Our ISMS serves as a steadfast assurance of our dedication to safeguarding information assets.
Certified and Globally Aligned
At Persistent, our comprehensive information security policies and procedures are anchored by our Information Security Management System (ISMS). We proudly maintain organization-wide certifications in:
- ISO 27001 for Information Security
- ISO 22301 for Business Continuity
- ISO 27701 for Privacy
- ISO 27017 for Cloud Data Security
- ISO 27018 for Privacy in the Cloud Environment
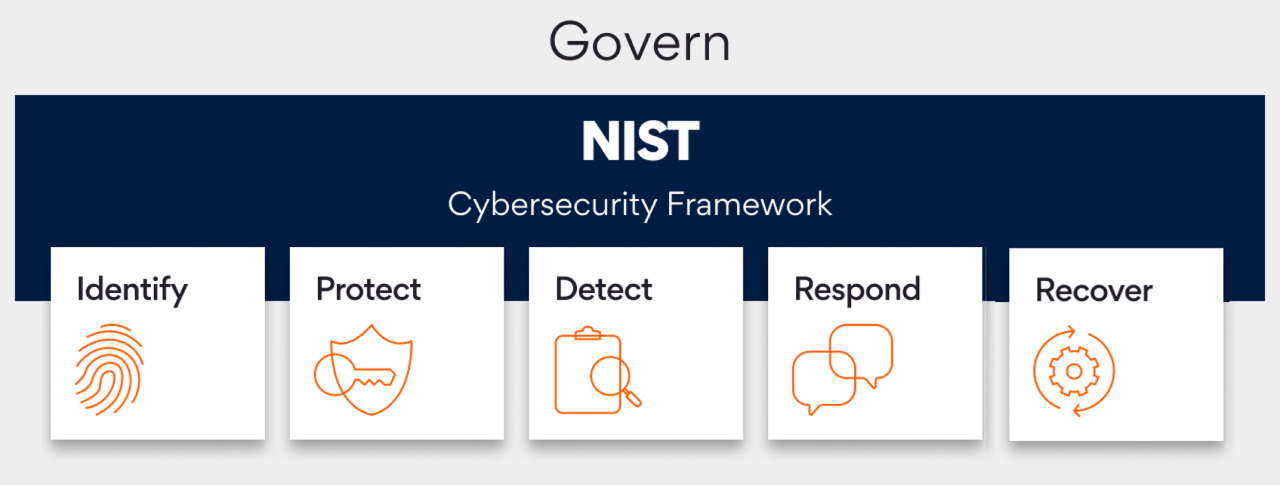
Additionally, we adhere to NIST and global standards for cybersecurity.
Information Security Governance
The Persistent Information Security Management System (ISMS) prioritizes information security governance, ensuring coordinated and organized efforts across all levels. Led by the Chief Information Security Officer (CISO), the ISMS team includes professionals specializing in Risk & Governance, Audit & Compliance, and Security Operations, supporting the CISO in overseeing information security within the company.
The CISO is responsible for cybersecurity, with clear accountability for IT security/cybersecurity. The Chief Information Officer (CIO) serves as the overall steward of information security, ensuring alignment with strategic goals and objectives. Together, they ensure appropriate governance measures are in place to safeguard against potential risks and threats.
Priority For The Board
The Persistent Board prioritizes information security and data privacy as a key responsibility toward the Company and its clients. It reviews the relevant risks on a quarterly basis, as reported by the Risk Management Committee. The Risk Management Committee receives quarterly updates about the information security risk posture from CISO Office, Operational IT risks from the Global IT function as well as attestation on the cyber security risk from the CRO office.
Information Security Program Highlights
Key features of our information security program include:
- Oversight and guidance from our Chief Information Security Officer, ensuring effective management of our information security and resiliency program.
- Mitigation of technical and operational risks associated with our information assets.
- Utilization of cutting-edge cybersecurity technologies to safeguard against evolving threats.
- Implementation of secure software development and testing practices.
- Streamlined change management processes to ensure coordinated and secure updates.
- Robust business resiliency planning, including thorough disaster recovery and business continuity testing.
- Regular internal and external security audits and vulnerability assessments conducted by both third-party vendors and internal staff.
- Continuous posture assessments to maintain a strong security stance.
- 24/7 monitoring of cybersecurity operations to detect and respond to threats promptly.
- Implementation of secure, Zero Trust-enabled role-based access controls to safeguard system integrity.
Information Security Policy
The board’s directives are effectively translated into an Information Security Policy by the Chief Information Security Officer (CISO). This policy delineates acceptable and unacceptable usage practices comprehensively. Persistent maintains a robust set of global IT Risk and Information Security policies, standards, and procedures, aligning with ISO and National Institute of Standards and Technology (NIST)
standards.
Included within the policy are general guidelines covering password protection, acceptable usage, email usage, and information security responsibilities. Compliance with this policy is obligatory for all Persistent entities, employees, and affiliated parties.
The policy undergoes annual review or revision whenever there’s a change in cybersecurity posture, with updates accessible to all employees through the intranet portal.
Robust Technology and Security Controls
The CIO and CISO office at Persistent have consistently maintained a steadfast commitment to standardization and systematic risk reduction. These controls encompass physical and environmental security controls to prevent unauthorized physical access, damage, and interference into Persistent’s facilities and information, as well as logical security controls to preserve the confidentiality, integrity and availability of information and the resources for processing it.
This commitment is exemplified by several key practices:
- Standardized Endpoint Controls: All Persistent Managed endpoints globally adhere to the same set of controls, ensuring consistent monitoring and management regardless of location.
- Centralized Onboarding and Offboarding Processes: Our onboarding and offboarding procedures are centrally managed through a common ERP system, guaranteeing uniformity and efficiency across the organization.
- Global Standardization of Physical and Environmental Controls: All locations worldwide adhere to the same standards of physical and environmental controls, as necessary.
- Multi-Factor Authentication (MFA) and Robust Password Policies: All corporate applications and identities are protected by MFA and employ ultra-complex, lengthy passwords to bolster security. Privileged access management is deployed for secure management of privileged identities and access.
- Implementation of Data Loss Prevention (DLP) Technologies: DLP technologies are in place to detect and prevent the unauthorized leakage of confidential data from both physical and logical boundaries.
- Unified Incident Management Processes: Incident management processes and playbooks are centrally managed and cover a wide range of incidents, including cyber, physical, and environmental impacts. Centralized monitoring ensures prompt response to any security incidents.
- Deployment of Zero Trust Architecture: Corporate applications are only accessible through a Zero Trust framework, and access to non-persistent endpoints is controlled through browser isolation to minimize operational impacts.
- Centralized Change Management: Infrastructure change management is guided by a centralized change advisory board, with predefined change windows and thorough verification of rollout plans. Emergency changes are subject to review by an emergency CAB before authorization and implementation.
Incident Management – Cyber Resilience at Persistent
Persistent’s CIO and CISO offices uphold a steadfast commitment to standardization and systematic risk reduction. This includes robust technology and security controls to safeguard our facilities and information from unauthorized access and interference, ensuring confidentiality, integrity, and availability.
Our cyber resilience philosophy adopts a dual strategy: investing in top-tier cybersecurity tools to prevent attacks, and prioritizing readiness with a proven recovery strategy in anticipation of potential incidents. Aligned with the NIST framework, we deploy best-in-class cybersecurity measures and maintain well-documented procedures to enhance organizational resilience against evolving threats.
Persistent operates a dedicated Security Operations Center (SOC) that oversees various processes, including monitoring, threat detection, incident response, and deep-web research. Proactively identifying and mitigating emerging threats, our SOC team remains vigilant.
Furthermore, we implement comprehensive initiatives to address evolving concerns, such as credential leaks, privileged access management (PAM), cloud security, and phishing prevention. Our incident handling protocols are meticulously documented and regularly reviewed.
In the event of an information security incident, our dedicated Security Incident Response Team (SIRT) promptly responds. Accessible through email and a dedicated intranet portal, employees and stakeholders can report incidents, with specialized response teams led by the SOC.
Moreover, we prioritize robust business continuity and disaster recovery planning to minimize disruptions. Regular drills and exercises validate our plans, ensuring compliance with ISO 22301 requirements and safeguarding network and communication services availability.
Securing the Human Firewall Through Awareness and Continuous
Training
We achieve continuous awareness training for all employees through the “Securing Persistent Initiative.” This initiative focuses on mitigating human elements in cybersecurity incidents and fostering collective responsibility for safeguarding our organization’s information assets. Employees including contractors receive ongoing education and skill development to effectively identify and address security risks.
Regular education and awareness sessions cover topics such as phishing prevention, password management, social engineering tactics, and data protection principles. This program cultivates a positive cybersecurity culture, improving cyber hygiene and stakeholder awareness of information security responsibilities.
Key policies and procedures implemented for all employees include:
- Internal availability of an information security/cybersecurity policy.
- Information security/cybersecurity awareness training, supported by evidence.
- A clear escalation process for reporting suspicious activity.
- Integration of information security/cybersecurity into employee performance evaluations and disciplinary actions.
The program utilizes various communication channels, such as newsletters, posters, and online training modules, to reinforce key security messages and foster a culture of awareness throughout the organization. Additionally, proactive technologies like phishing simulations, Pawnage monitoring, Zero Trust, UEBA (User Entity Behavior Analysis), and access management help mitigate risks from the human attack surface while reducing user fatigue. Continuous assessments are conducted for all stakeholders to measure their awareness levels.
Robust Cybersecurity Vulnerability, Audit and Compliance Monitoring Processes
To enhance assurance levels, our Information Security Management System (ISMS) is equipped with well-defined verification and control mechanisms. These include continuous supervision and monitoring processes, which are consistently active and encompass:
- Security and network monitoring processes to ensure compliance with security regulations across networks and information systems.
- Implementation of Zero Trust and validation processes to monitor and verify users and systems before connecting to Persistent information assets, ensuring compliance with information security regulations.
- Audits of platform and application technical vulnerabilities to identify and assess security risks. External vulnerability assessments and penetration testing by reputable third parties including simulated attacks provide continuous assurance of our robust security posture.
- Annual assessments by a third-party organization for SOC 2 Type II compliance, focusing on the Trust Service Principles of Security, Confidentiality, and Availability.
- Continuous internal audits for customer projects, assessing customer requirements, adherence to Persistent information security policies and procedures, and customized risk-based audit strategies to enhance project security.
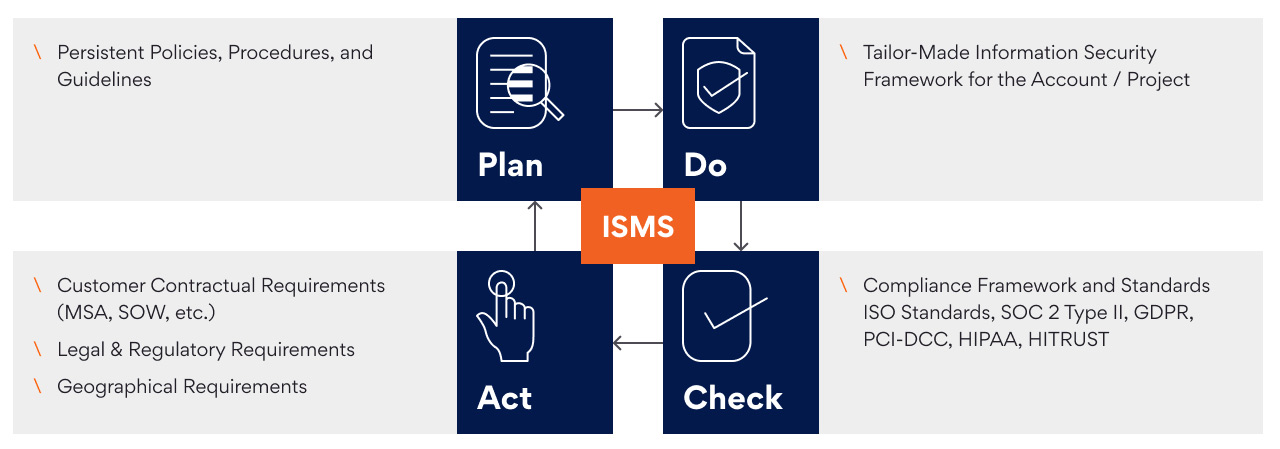
We view security as an ongoing activity and remain committed to improving our security posture as we evolve and expand our business. Customers can trust that we will maintain continuous compliance and provide top-notch support to our business processes and systems.
Contact us
(*) Asterisk denotes mandatory fields