
Data Privacy
Privacy and Data Protection at Persistent Systems
As a global software development company specializing in both products and services across various industry verticals, Persistent adheres to rigorous contractual and regulatory obligations applicable to itself and its customers. This encompasses compliance not only within the jurisdictions where Persistent operates but also where its clients are situated. Persistent handles intellectual property (in the form of designs, architecture, and code) of its customers as well as the data of its customers and, on several occasions, the data of the customers’ customers. Such datasets often contain sensitive privacy information and data, underscoring the critical importance of secure data processing. Persistent is deeply committed to upholding the highest standards of privacy and data protection. This commitment is demonstrated through the establishment and maintenance of a comprehensive Privacy Information Management System (PIMS).
Management Commitment to Privacy
The Persistent Privacy Policy delineates the company’s objectives concerning privacy management and underscores management’s unwavering commitment to privacy protection. The application of this policy is mandatory for all group companies, business lines, subsidiaries, and affiliates, including all operations performed on personal data. All employees and third-party entities (Suppliers, Vendors, etc.) associated with Persistent are obligated to adhere to this policy. Furthermore, it extends its jurisdiction to encompass all information systems and facilities involved in the processing and storage of personal data, encompassing not only internal systems owned by the company but also those employed in operations and projects executed on behalf of its customers. An excerpt of the Privacy policy is available here.
Approach to sustained data privacy compliance.
Acknowledging the importance of addressing privacy concerns comprehensively in conjunction with information security protocols, Persistent established its Data Protection Office (DPO Office) within the Chief Information Security Officer (CISO) office in 2016. Under the leadership of the Data Protection Officer (DPO), the DPO Office is tasked with ensuring the implementation of robust data privacy controls and procedures to mitigate privacy and data protection risks faced by the company. Persistent promptly aligned its privacy policies with the requirements outlined in the EU General Data Protection Regulation (GDPR) in 2017, and subsequently, with other relevant legal frameworks. In 2021, the company adopted ISO 27701 – Privacy Information Management System (PIMS) to facilitate seamless and sustainable compliance with data privacy regulations and operations across all operational regions. Today, Persistent holds certification against ISO 27701 as both a Controller and Processor of Personal Information, affirming its commitment to safeguarding data privacy throughout its operations.
Privacy Information Management Systems (PIMS)
The Persistent Information Management System (PIMS) seamlessly integrates policies, procedures, and cutting-edge technologies to ensure strict adherence to regulatory mandates and industry standards. Our approach incorporates rigorous Technical & Organizational Measures (TOMs) meticulously designed to address privacy obligations and bolster security measures, in alignment with both regulatory mandates and client-specific requirements. In navigating the complex landscape of legal statutes and client obligations, PIMS goes beyond mere compliance, embracing both data controller and data processor responsibilities.
We steadfastly uphold the fundamental principles of data privacy, including:
- Lawfulness, Fairness, and Transparency
- Limitations on Purposes of Collection, Processing, and Storage
- Data Minimization
- Accuracy of Data
- Data Storage Limitations
- Integrity and Confidentiality
The PIMS thus ensures a comprehensive compliance framework across all operational dimensions. These principles are tightly integrated with the Technical and Operational controls implemented across the data lifecycle of Privacy related data at Persistent.
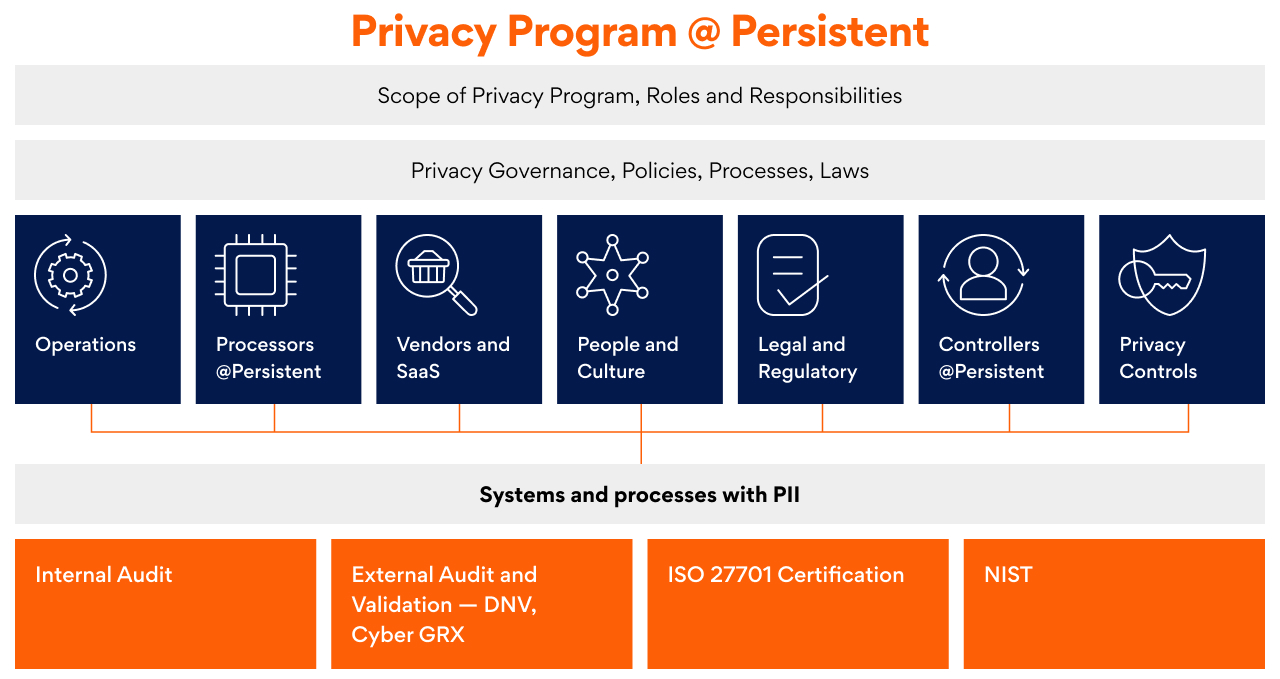
At the core of our PIMS program lies a dedicated team responsible for vendor due diligence, contract reviews, and the implementation of essential documentation, including Records of Processing Activities (ROPA) and Privacy Impact Rating of personal information processed as a controller. Central to this commitment is the meticulous maintenance of comprehensive documentation, comprising a detailed Privacy Policy, PIMS manual, privacy notices, data privacy assessment process including Data Protection Impact Assessment (DPIA), Legitimate Interests Assessment (LIA) & Transfer Impact Assessment (TIA), privacy by design & default checklist for applications development, Data Subject Rights procedure, and more. Our proactive approach extends to conducting thorough privacy risk assessments, encompassing functional, operational, and account/project specific factors, to ensure robust management and continuous validation of privacy protocols.
Data Privacy Governance Framework
At Persistent, the dedicated Data Protection Office serves as both architect and overseer, while Business Enabling Functions and units are responsible for implementation. Periodic independent audits are conducted by our Internal as well as external entities, to verify the efficacy of our data privacy measures. The role of Privacy Officer is designated to the Data Protection Officer (DPO), who reports to the Chief Information Security Officer (CISO).
Ongoing Senior Management reviews, led by the Chief Information Security Officer (CISO), Chief Information Officer (CIO), and Chief Risk Officer (CRO), ensure thorough oversight of our privacy practices.
The Persistent Board considers information security and data privacy paramount responsibilities towards both the Company and its clients. The Risk Management Committee (RMC) of the board quarterly reviews Persistent’s privacy and data security risks besides other Enterprise Key risks. This review also includes deep dive on both privacy and data security risks. This oversight helps them to understand and validate the various mitigation measures taken and planned in response to the emerging risks and evolving regulatory requirements. The Chief Information Officer (CIO) is an integral member of the Risk Management Committee of the board while the Chief Risk Officer (CRO) presents these risks for the RMC oversight.
Technical and organizational Measures
Persistent employs robust and effective technical and organizational measures (TOMs) to safeguard personal data against unauthorized or unlawful access, use, disclosure, alteration, or destruction. These measures are tailored to the specific context, purpose, and scope of data processing activities, encompassing the following:
- Robust Technology and security controls: Detailed descriptions of these controls are available on our Information Security page, accessible here.
- Data Protection Measures: Within our PIMS framework, we implement robust measures such as data classification, access controls, encryption protocols, and ongoing monitoring to mitigate privacy risks and safeguard personal data throughout its lifecycle.
- Security Protocols: Persistent enforces stringent security protocols to ensure privacy and prevent unauthorized access or breaches. These measures include encryption protocols, encryption/de-identification techniques, access controls, vulnerability assessments, and intrusion detection systems, fortifying our defenses and minimizing the risk of data breaches.
- Privacy by Design and Default: Our application development processes embed strategies, guidelines, and validations to promote responsible data-centric innovation in compliance with data privacy regulations, meeting both end-user and client expectations. Privacy enhancing technologies (PETs) such as Data Encryption at rest and in motion, Differential privacy, Anonymization, data minimization and purpose limitation techniques are used to further enhance data security and privacy compliance.
- Lawful Basis for Processing: As a controller of personal data, Persistent relies on explicit consent or a legal basis for the collection and retention of personal data in accordance with our privacy policy. When acting as a processor, our customers determine the appropriate legal basis for processing activities. We retain personal data to comply with retention or statutory limitations or for contractual purposes only, safeguarding and limiting active use where technical limitations prevent deletion or anonymization. Persistent is a software development company and we do not use customer data for any other secondary purposes nor rent, sell, or provide personal data to third parties for purposes other than completing transactions/services.
- Data Protection Impact Assessments: These assessments are conducted for every new process or when there is a change in existing processes involving the processing of personally identifiable information (PII) or sensitive personal information (SPI), ensuring secure and compliant processing across the delivery lifecycle.
- Compliance Assurance: In adherence to regulatory mandates, Persistent maintains transparent processes for handling Data Subject Rights Requests (DSRRs), providing prompt and compliant responses to individuals inquiries regarding their personal data. Privacy notices are provided at the time of data collection for both internal and external data subjects, with privacy statements available publicly to external data subjects. These notices and statements are regularly updated to reflect changes in personal data processing or Data Privacy regulations.
- Training and Awareness: Persistent invests in comprehensive training and awareness programs to educate employees on privacy best practices, regulatory requirements, and their roles and responsibilities in protecting personal data. Our privacy program remains adaptive and responsive to evolving requirements by monitoring emerging privacy regulations and industry trends, incorporating key learnings from incidents into privacy awareness initiatives. A Zero tolerance policy with punitive and/or disciplinary actions in case of breach is in place with acceptable usage and Privacy consent being secured from all users of the information systems and assets at Persistent.
- Third Party and Vendor Data Privacy: Given the increasing reliance on outsourcing, including cloud service providers, for both Persistent and our customers, managing supply chain risk and vendor data privacy has become strategically significant. We have comprehensive guidelines for suppliers/vendors to adhere to strict obligations imposed under contracts and applicable laws. Technical and operational controls are established through contracts with third-party data processors and sub-processors, ensuring sufficient guarantees and obligations regarding data protection and security.
Robust incident management and breach handling
At Persistent, we maintain robust mechanisms for detecting, assessing, containing, and managing data privacy breaches and incidents. Our well-defined processes and procedures ensure timely responses to breach notification obligations in accordance with applicable laws. In cases where an incident or breach is deemed to have a high impact or is mandated by law, affected data subjects and/or supervisory authorities are promptly notified. We implement well-established processes and playbooks through our 24x7x365 Security Operations Center to address such data breach incidents effectively. For more information on our cyber resilience practices, please visit our Cyber Resilience page.
During the fiscal year of 2024, no substantiated complaints regarding breaches of customer privacy were received from external parties or regulatory authorities. Additionally, no breaches were identified within the reporting period that occurred external to the organization, and all instances where users were affected by breaches were promptly notified.
Channel for exercising rights and reporting incidents.
Persistent has established a well-defined process to address data subject rights requests within specified timelines. Data Subjects are offered Right of access, rectification and deletion of individuals’ data as outlined in the Privacy policy. Data subjects may exercise their rights or report incidents related to privacy by contacting the Data Protection Officer at privacyofficer@persistent.com.
Certifications
Our commitment to safeguarding personal data remains steadfast, aligning with client expectations and regulatory mandates. We are proud to be among the pioneering organizations globally certified with accreditation for the ISO 27701 privacy information management standard. This dedication is further underscored by our other certifications:
- ISO 27701:2019 – Privacy Information Management System
- ISO 27018:2019 – Securing Personal Data in Cloud
- System and Organization Controls (SOC) 2 Type 2
Through these certifications and ongoing compliance efforts, Persistent demonstrates its unwavering commitment to transparency, integrity, and excellence in privacy and security practices. This commitment instills confidence in our stakeholders and reinforces our position as a trusted industry leader.
External Privacy Assurance and Audits
Persistent maintains ongoing ISO 27701 and ISO 27018 certification for our Privacy Information Management System (PIMS). Our PIMS undergoes routine internal audits conducted by our Infosec compliance team to ensure consistent compliance.
Furthermore, external independent audits are carried out annually to fulfill the requirements of ISO 27701 and ISO 27018. In addition, we undergo annual evaluations by a third-party organization to attain SOC 2 Type II compliance. These evaluations center on the Trust Service Principles of Availability established by the American Institute of Certified Public Accountants (AICPA), providing further assurance of our unwavering dedication to upholding elevated standards of privacy and data security.
Contact us
(*) Asterisk denotes mandatory fields