
Persistent Intelligent Cyber Recovery
Recover from today’s worst Cyberattacks rapidly and securely, going beyond traditional cloud disaster recovery and ransomware recovery solutions.
Ransomware Threat Landscape
76%
Of global organizations paid ransom in 2021
24%
Of those could not recover their data
21 Days
The average downtime organizations face due to ransomware attacks
66%
Of global organizations were the victim of ransomware attack in 2021

How to recover from ransomware attacks at scale
Download whitepaperRansomware encryption and other emerging cyberattacks, such as zero-day attacks, continue to evolve, developing new methods to circumvent existing security controls. Traditional Backup and Disaster Recovery solutions were not designed for recovery from cyberattacks. It takes more than a product to be a complete cyber recovery solution. Businesses must find solutions to restore business continuity with as little data loss as possible and as rapidly as possible.
Persistent Intelligent Cyber Recovery (PiCR) is not just another disaster recovery solution. Together with Google Cloud, we have created a cyber recovery offering to enable faster yet safe recovery from cyberattacks. The approach includes customized process development, cutting-edge technologies – leveraging Actifio, Google Cloud Platform, and Persistent IPs – and managed cyber recovery and operations. Persistent Intelligent Cyber recovery (PiCR) provides an environment for secure recovery and return to operations by leveraging network isolation, immutable storage, and Intelligent analysis and detection.
Benefits
- Avoid costly creation of in-house recovery services and instead leverage decades of expertise in recovery and cyber resilience
- Accelerate the recovery times of business-critical applications using proven IP & assets without having to “pay the ransom"
- Detect and eliminate attackers with robust anomaly detection to identify the early signs of attack and take action before attackers gain a foothold
- Leverage expert advice to evaluate your business and technology stack, creating customized data protection solutions for your organization
- Prepare for the worst cyber attackers can throw at you by implementing disaster recover using secure cloud services backed by Google Cloud

Want to see Persistent Intelligent Cyber Recovery (PiCR) solution in action?
Watch Demo videoPiCR – Deployment Overview
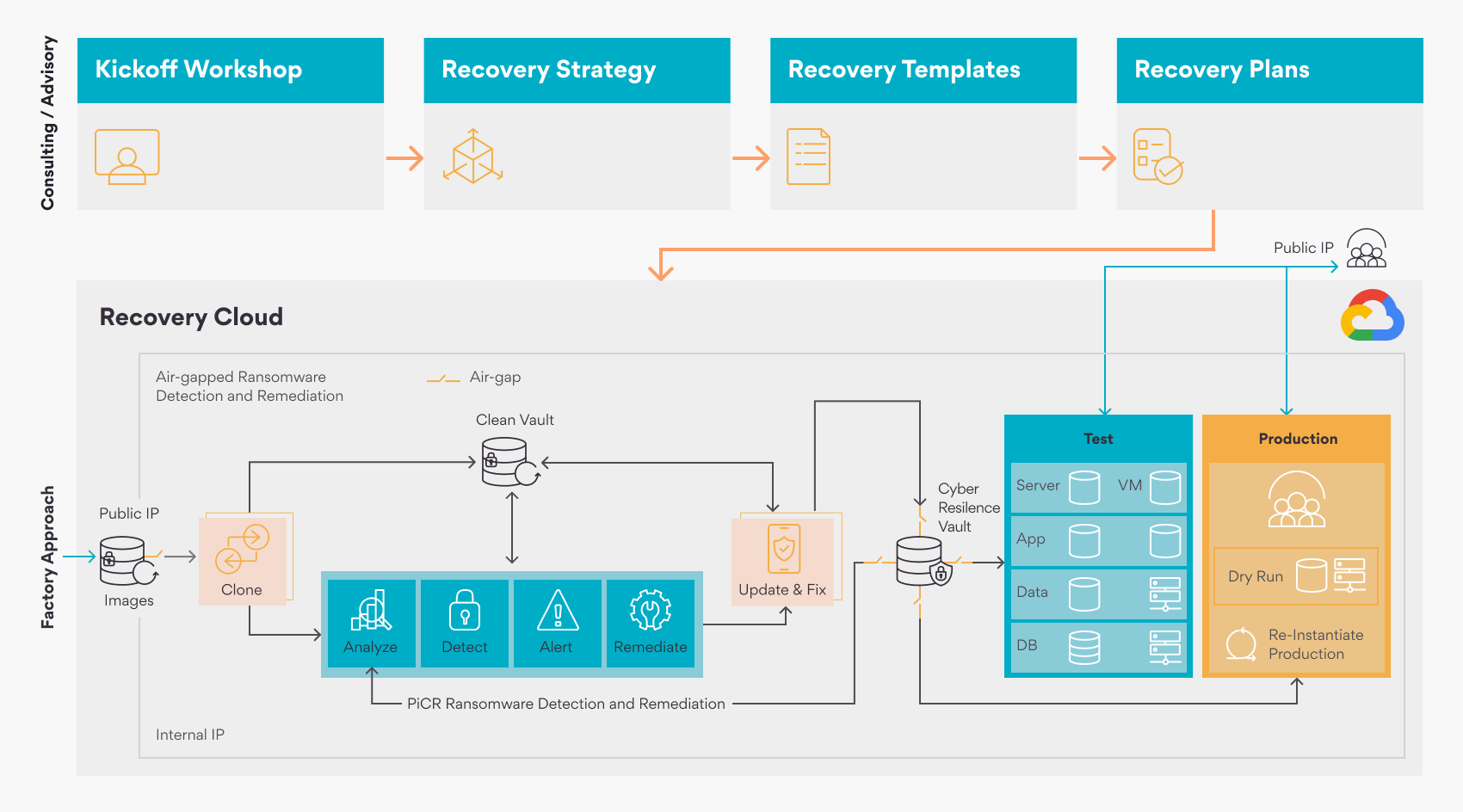

Take proactive steps so your organization will be ready to rapidly respond and recover from incidents with limited downtime
Read solution briefWhy Persistent?
Secure, Protected, & Resilient
Our comprehensive cybersecurity solutions empower organizations to maintain operations seamlessly, even in compromised IT environments, while proactively anticipating and mitigating emerging risks. We enable businesses to thrive in an increasingly complex and interconnected digital world, ensuring their infrastructure remains secure, safeguarded, and resilient against evolving threats.
Our Experience
Persistent, with more than 33 years of experience developing security defense strategies, is a cybersecurity journey partner for leading enterprises and global brands. Our end-to-end security services enable enterprises to factor in blind spots and confidently defend their businesses against evolving threats. We have a mature cyber security practice, comprising in-house IPs and accelerators.
Partner Ecosystem
With a comprehensive 360-degree relationship as a trusted training, engineering, certification, and implementation partner, we collaborate closely with leading global security providers. Backed by 60+ alliances and 7 strategic partnerships, we deliver end-to-end security solutions that drive innovation and safeguard enterprises in a rapidly evolving digital landscape.
Related Offerings & Solutions
-
Cloud & Infrastructure
-
Enterprise IT Security
-
Enterprise IT Security
Contact us
(*) Asterisk denotes mandatory fields











