Get your Independent Cyber Attack Risk Assessment

Improving your organization's cyber resilience quickly.
Randori is one of the best Attack Surface Management (ASM) solutions that provides continuous discovery, analysis, remediation, and monitoring of the cybersecurity vulnerabilities and potential attack vectors that make up an organization’s attack surface. We enable you to build red teaming capabilities at a fraction of the cost of a traditional red team. In the current environment of rapidly evolving cybersecurity threats, offensive security is the best way to stay ahead of bad actors. We help you build a best-in-class offensive security program through a combination of Attack Surface Management (ASM) and Automated Red Teaming.
Get your Independent Cyber Attack Risk Assessment
of Security Leaders Say Red Teaming is the Best Practice for Risk Assessment & Reduction
of organizations have experienced an attack due to an unknown asset (Shadow IT)
of assets are unknown or unmanaged to an organization due to rapid transformation
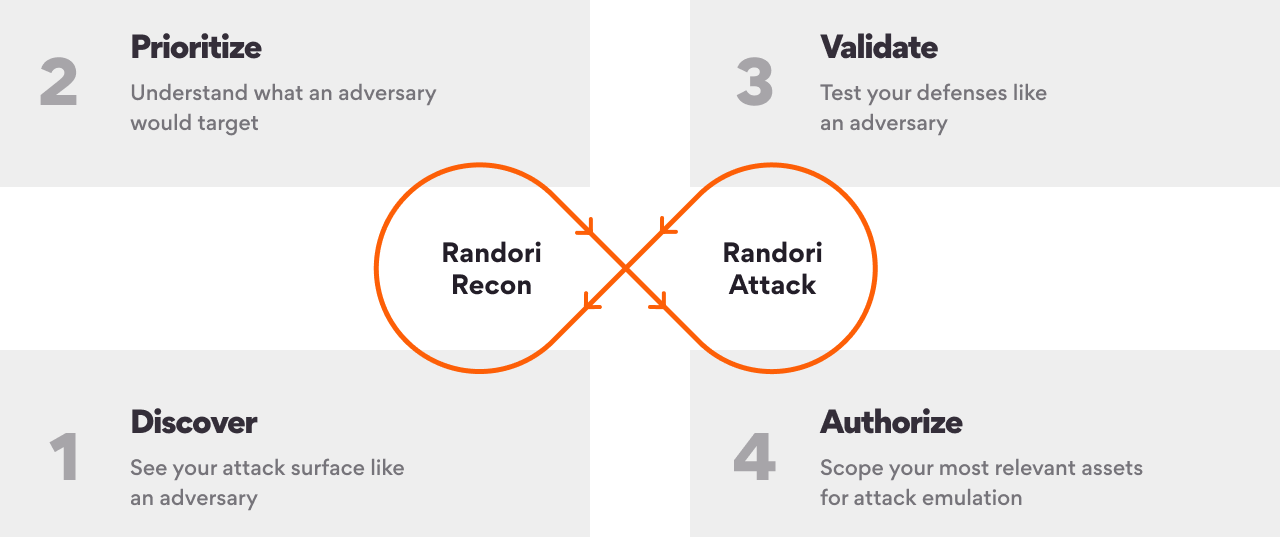
Asset discovery automatically and continuously scans for and identifies internet-facing hardware, software, and cloud assets that could act as entry points for a hacker or cybercriminal trying to attack an organization.
Once assets are identified, they are classified, analyzed for vulnerabilities, and prioritized by ‘attack ability‘—essentially an objective measure of how likely hackers are to target them.
Applying appropriate security controls to the asset in question and bringing previously unknown assets under control
Continuous monitoring to detect and assess new vulnerabilities and attack vectors in real- time, and alert security teams to any new vulnerabilities that need immediate attention.

Reduce blind spots by identifying externally exposed on-premises or cloud assets
Make informed decisions about the risk by gaining insights
Discover the real-world attach patterns and techniques that are more likely to be exploited
20+ years of proven expertise as IBM’s Partner for Security Products.
500+ professionals working on IBM Security Products. Our experts share insightful perspectives and optimal strategies for handling cybersecurity.
We have a global team of experts to remediate the issues found as well.
Randori Recon review in ‘Security Solutions – Others’ (gartner.com)

20+ Years
Of Successfull Partnership
2,000+
Engineers Dedicated to IBM work
400+
Shared Customers
115
Active Engagements Annually
600+
IBM Badges
(*) Asterisk denotes mandatory fields
(*) Asterisk denotes mandatory fields